The U.S. National Institute of Standards and Technology (NIST) updated its Cybersecurity Framework (CSF 2.0) in February this year from the earlier 2014 version.
The new guidelines are designed to strengthen the data security posture of organizations in an era of growing cyberthreats. Forrester’s Security Survey for 2023 puts it into context citing data that reveals that 77% of security decision-makers experienced at least one data breach at their firm over the past 12 months.
In this scenario, the CSF 2.0 has expanded guidance to include all organizations — including industry, government, academia, and nonprofit — regardless of its size, sector, or maturity, so as to manage their cybersecurity risks. The framework can be used by organizations to understand, assess, prioritize, and communicate its’ cybersecurity efforts.
The New Govern Function
As part of changes in the CSF 2.0, a sixth function called Govern has been added, underscoring the importance of governance in cybersecurity. This supports IT and security leaders’ ability to establish a risk management strategy, create security programs based on risk and increase organizational engagement in cybersecurity programs and risk ownership. The function creates opportunities for achieving greater program support and funding through policy creation. Cybersecurity is emphasized as a major component of the organizational strategy. The function delves into policy making, defining roles, responsibilities, and authorities around cybersecurity. Third-party vendor risks are managed under Supply Chain Risk Management.
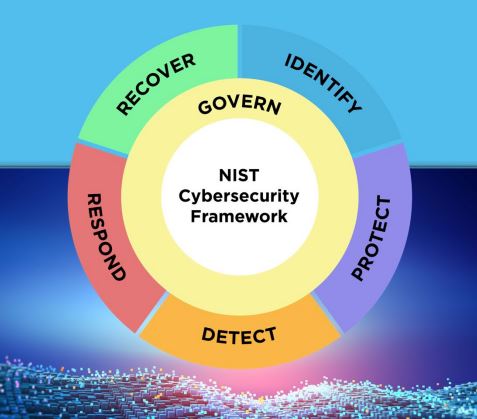
Cybersecurity Framework Components
An organization can use the CSF Core, Profiles, and Tiers to understand, assess, prioritize, and communicate cybersecurity risks.
The CSF Core components consist of Functions – Govern, Identify, Protect, Detect, Respond, and Recover that are further divided into categories and subcategories. The Core establishes a framework that can help an organization manage its cybersecurity risks.
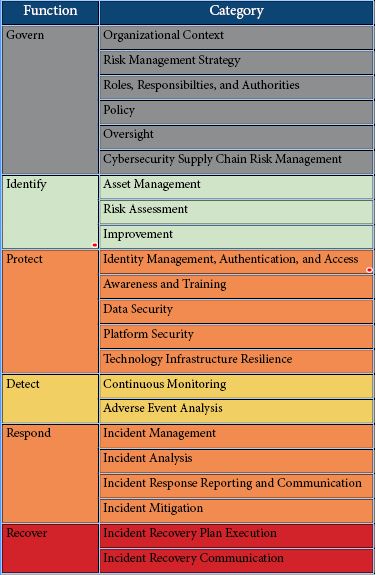
Govern — The organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.
Identify — The organization’s current cybersecurity risks are understood. This includes organization’s assets such as data, hardware, software, systems, facilities, services, people, suppliers, and related cybersecurity risks.
Protect — This function includes safeguards to manage the organization’s cybersecurity risks. The function supports the ability of an organization to secure the identified assets to prevent or lower the likelihood and impact of adverse cybersecurity events, as well as to increase the likelihood and impact of taking advantage of opportunities. Outcomes covered by this Function include identity management, authentication, and access control; awareness and training; data security; platform security (i.e., securing the hardware, software, and services of physical and virtual platforms); and the resilience of technology infrastructure.
Detect — Under this function, possible cybersecurity attacks and compromises are found and analyzed. Detect enables the timely discovery and analysis of anomalies, indicators of compromise, and other potentially adverse events that may indicate that cybersecurity attacks and incidents are occurring. This Function supports successful incident response and recovery activities.
Respond — This function highlights the actions to contain the effects of cybersecurity incidents. Outcomes within this Function cover incident management, analysis, mitigation, reporting, and communication.
Recover — In Recover, the assets and operations affected by a cybersecurity incident are restored. Recover supports the timely restoration of normal operations to reduce the effects of cybersecurity incidents and enable appropriate communication during recovery efforts.
Actions that support Govern, Identify, Protect, and Detect should work in tandem, while actions that support Respond, and Recover should be in alert and ready state.
The organization should apply these to all Information and Communication Technologies (ICT) including information technology (IT), the Internet of Things (IoT), and operational technology (OT). Application can also include all technology environments such as cloud, mobile, and artificial intelligence systems.
CSF Organizational Profiles describe an organization’s current and/or target cybersecurity posture in terms of the CSF Core’s outcomes. An organizational should consider its’ mission, objectives, stakeholder expectations, threat landscape, and requirements while creating these profiles.
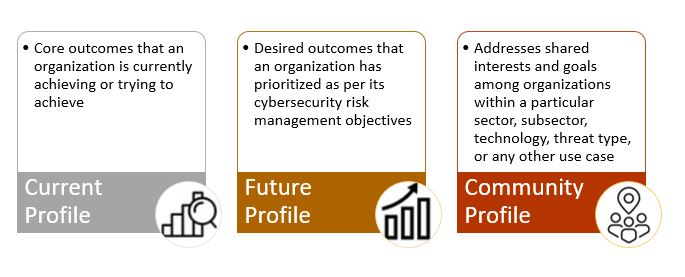
CSF Tiers are applied to CSF Organizational Profiles to measure the organization’s cybersecurity risk governance and management practices. Moving to a higher Tier is encouraged when risks are greater or when a cost-benefit analysis indicates that cybersecurity risks can be effectively reduced.

Tiers provide a framework for organizations to enhance their cybersecurity approach and identify potential vulnerabilities and weaknesses in their cybersecurity infrastructure.
Conclusion
With the integration of data-driven technologies, such as AI, the level of sophistication of cybersecurity threats is increasing and also becoming widespread. Organizations that strive to address internal weaknesses by creating robust cybersecurity protocols and infrastructure will have a substantial advantage over those that do not.
The new Govern function hinges on developing an actionable cybersecurity strategy. Cybersecurity-mature organizations will have established measures and protocols that account for the latest advancements in the threat and technology landscape. Oversight and compliance will be important factors while creating an overall risk strategy and enterprise risk management.
NIST CSF creates an opportunity for IT and security leaders to accelerate investments in risk-driven cybersecurity strategies that can lead to improving security outcomes. The CSF is forward-looking and intended to apply to future changes in technologies and environments.